Alternatives to Passwords
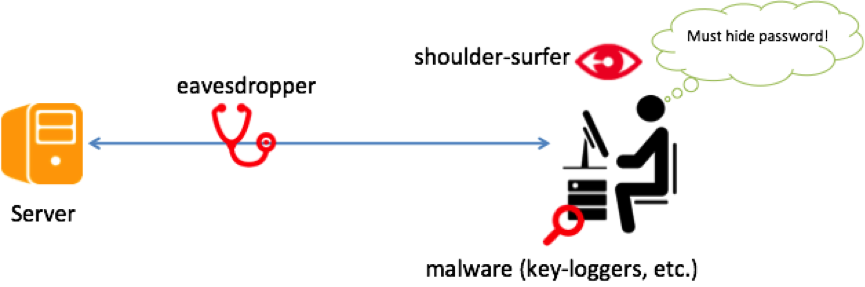
Passwords are susceptible to observation, i.e., someone watching a user, either directly or through a hidden camera, typing his/her password can successfully impersonate the user.
An alternative to passwords that is secure against observation yet maintains usability is an important goal. The aim of this project is to develop such alternate authentication schemes.
At present our research is in two main areas.
Cognitive Authentication Schemes
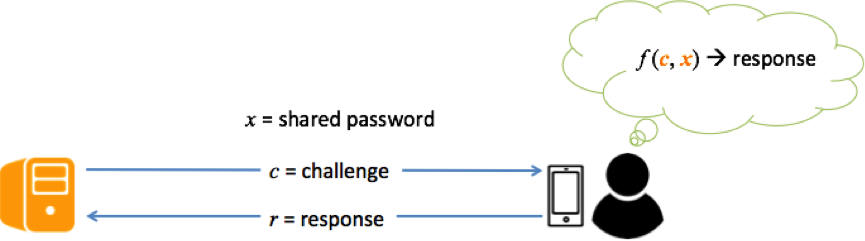
Cognitive authentication schemes employ human cognitive abilities to authenticate. The server sends a challenge to the user who responds by mentally computing a function of the challenge and the password. We can think of the responses generated as dynamic passwords.
Our research in cognitive authentication schemes is further divided into two directions
- Design new and usable cognitive authentication schemes
- Security analysis of existing cognitive authentication schemes to propose new attacks that will help us build more secure schemes in the future
Continuous and Implicit Authentication
Another alternative to passwords is to use an implicit and continuous authentication system. The system is implicit because of it can authenticate users based on the actions they would carry out anyway while using their devices. The system is continuous because it runs in the background without disturbing the user. The system only asks the user to enter password if an intrusion is detected.
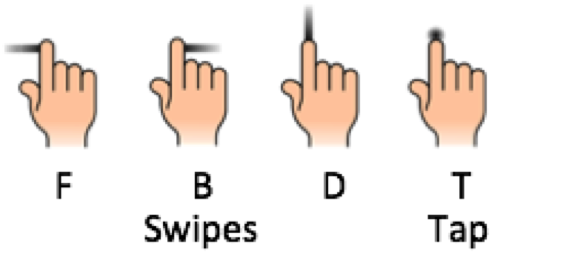
Our current work shows that implicit and continuous authentication is feasible on smart glasses. Our system looks at the touch gestures (taps and swipes) on the touchpad of the smart glass to see if they match the pattern of the user or an intruder.
Recent Publications
- Hassan Jameel Asghar, Ron Steinfeld, Shujun Li, Dali Kaafar, Josef Pieprzyk 2015, On the Linearization of Human Identification Protocols: Attacks based on Linear Algebra, Coding Theory and Lattices. IEEE Transactions on Information Forensics and Security, vol. 10, no, 8, pp. 1643-1655, April, 2015.
- Jagmohan Chauhan, Hassan Jameel Asghar, Mohamed Ali Kaafar, Anirban Mahanti 2015, Gesture-based Continuous Authentication for Wearable Devices: the Google Glass Case. Under submission.
- Hassan Jameel Asghar and Mohamed Ali Kaafar 2015, When are Identification Protocols with Sparse Challenges Safe? The Case of the Coskun and Herley Attack. Under submission