TrustStore
TrustStoreTM
We cannot take the things we treasure with us everywhere we go. Sometimes we do not even have room to keep them at home. That is why storage sheds and safety deposit boxes exist. With the masses of data that we store, we need very, very big storage sheds, which we now call the Cloud.
When we are talking about storing a huge amount of data, the shed needs to be more like a safety deposit box. This presents a problem, because systems can be hacked, and data stored in the Cloud has been shown to be vulnerable. Over the last few years there have been some high-profile, large-scale privacy leakages. For example, in 2015 the security of extramarital affair facilitation site Ashley Madison was breached, with 37 million records stolen – names, addresses and credit card information, which caused the site is users a lot of grief, not to mention embarrassment.
Cloud storage is generally supplied by third parties: the economies of scale storage providers can achieve are an integral part of the business model. As a result, there is an inherent risk that confidential data may be vulnerable, either to third parties on the cloud or to the cloud provider itself.
How can we increase the confidence to store the huge amounts of information in cloud?
Our Solution (TrustStoreTM):
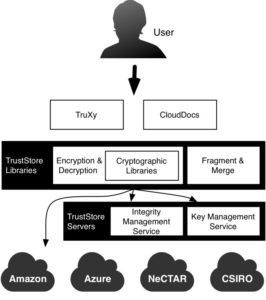
Cloud storage services are not secure by nature. There is an inherent risk of (a) data exposure (confidentiality), (b) data tampering (integrity) and (c) denial of access to data (availability). Any secure storage system should satisfy three basic properties: Confidentiality, Integrity and Availability (CIA). We provide a service-oriented solution for provisioning secure storage service in the hybrid cloud environment, called TrustStore.
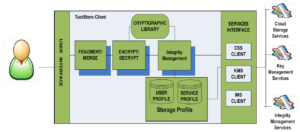
The system is suitable to facilitate individual as well as collaborative data storage and access. It satisfies CIA properties.
Confidentiality: It protects sensitive information from unauthorized parties including even a cloud storage provider.
Integrity: The change of the contents detected by a cryptogrpahic hash-function.
Availability: Authorized readers and writers can decrypt the encrypted data on the cloud.
The key technique of TrustStore is encryption and fragementation. To store the sensitive information on the third party cloud storage. TrustStore first divide the inforamation into several blocks. Each fragment is separately encrypted and store in distributed storages for further security.
That is, when the information consisting of “ABC” is uploaded to Data Storage (i.e. cloud storage). TrustStore fragmented this information into separate block “A”, “B” and “C”. Each block encrypted “#”, “^” and “%” using cryptographic algorithms and upload into Data Storage. The download process is the reverse of the upload process.
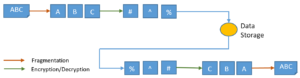
The encrypted data fragments are distributed randomly onto cloud storages. The data storages are not a single cloud storage (or provider), but they are comprised of multiple storages which can be distributed. This significantly reduces the risk of leakages. Unless all storage providers are jeopardized at the same time, whole information cannot be revealed.
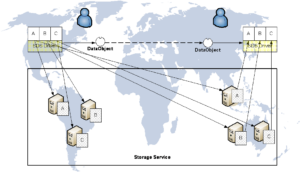
TrustStore is ready to use in a real-life. It supports main cloud storages such as Amazon S3, Microsoft Azure, NeCTAR and Rackspace. Moreover, it is already licensed to SME or integrated with our commercial/academic partners.
TrustStore provides different client APIs to integrate with different platforms. The current client supported by TrustStore includes: Java, C#, Python and Object C.
Our Partners
University of Melbourne: TrustStore is also used for a research community. It re-designed as TruXy to be fitted with scientific activities come from the post-genomic life sciences and specifically to support the endocrine genomics virtual research laboratory (endoVL). This project was funded through the Australian National eResearch Collaborative Tools And Resources (NeCTAR).
VeroGuard Systems: TrustStore is licensed commercially to a leading online payment company VeroGuard Systems. It is being integrated for an un-hackable cloud combined with VeroGuard.

Publications
- Shiping Chen, Surya Nepal, Jonathan Chan, David Moreland, John Zic: Virtual Storage Services for Dynamic Collaborations. WETICE 2007: 186-191 (The best paper award)
- Shiping Chen, Surya Nepal, Jonathan Chan, David Moreland, John Zic: A Service-Oriented Architecture to enable virtual storage services: a dynamic collaboration context. IJAHUC 4(2): 95-107 (2009)
- Jinhui Yao, Shiping Chen, Surya Nepal, David Levy, John Zic: TrustStore: Making Amazon S3 Trustworthy with Services Composition. CCGRID 2010: 600-605
- Surya Nepal, Carsten Friedrich, Leakha Henry, Shiping Chen: A Secure Storage Service in the Hybrid Cloud. UCC 2011: 334-335
- Surya Nepal, Shiping Chen, Jinhui Yao, Danan Thilakanathan: DIaaS: Data Integrity as a Service in the Cloud. IEEE CLOUD 2011: 308-315
- Surya Nepal, Richard O. Sinnott, Carsten Friedrich, Catherine Wise, Shiping Chen, et al.: TruXy: Trusted Storage Cloud for Scientific Workflows in Galaxy, IEEE Transactions on Cloud Computing (online).
- Catherine Wise, Carsten Friedrich, Surya Nepal, Shiping Chen, Richard O. Sinnott: Cloud Docs: Secure Scalable Document Sharing on Public Clouds. CLOUD 2015: 532-539
Contact
Surya Nepal PhD
Principal Research Scientist | Distributed Systems Security
DATA61 | CSIRO
PO Box 76, Epping NSW 1710
T +61 2 9372 4256
