IoT Security
Security and privacy protections are needed to increase the confidence on the wide deployment of Internet of Things (IoT) applications. Resource constrained IoT devices has limited computational power and battery lifetime. Such devices are desired to use affordable security solutions to guarantee data security as well as providing a long service period. In this project, we devise a secure mutual authentication protocol based on the lightweight public key based cryptography with post-quantum security.
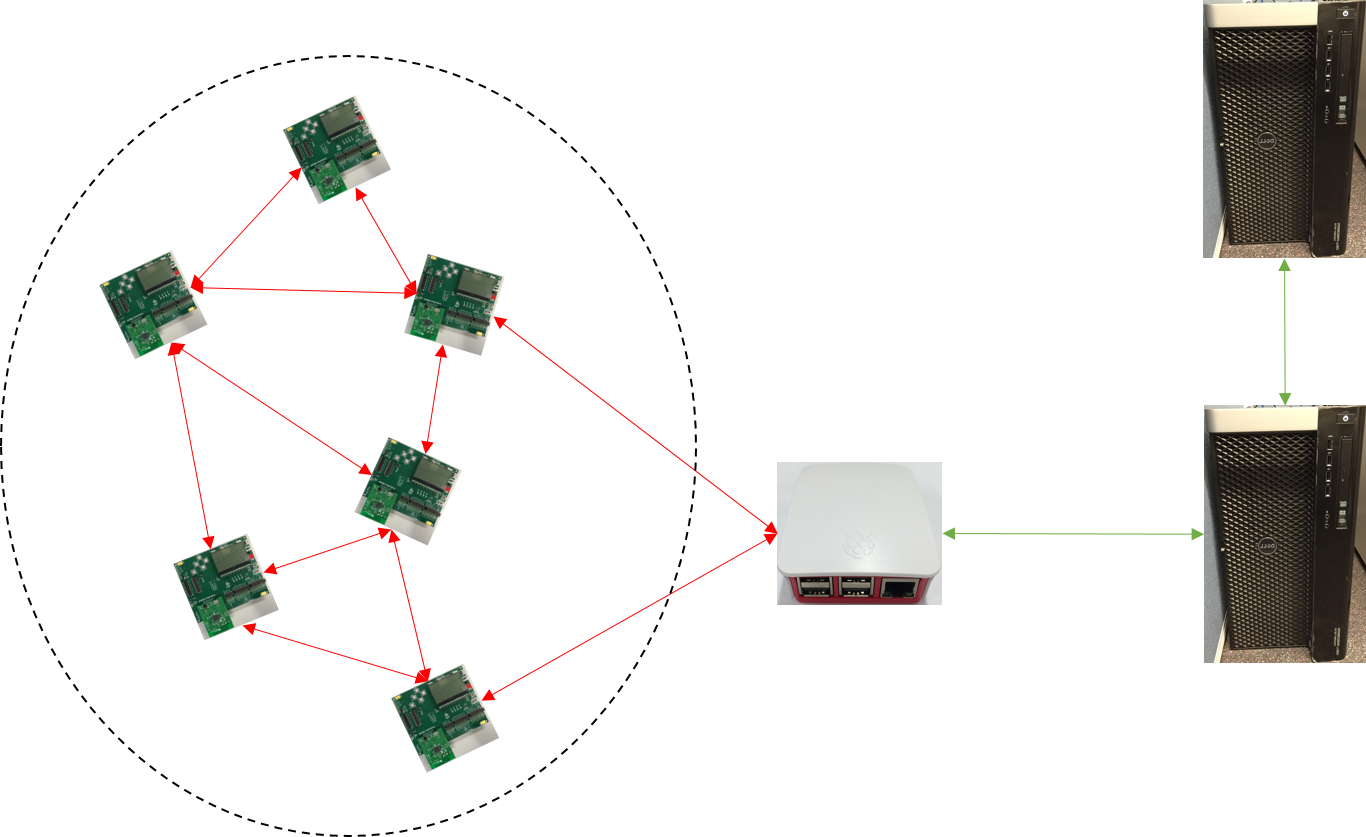
Fig 1: An IoT System Architecture
Background
The Internet of Things (IoT) provides transparent and seamless incorporation of large number of heterogeneous and different end systems. IoT applications are widely deployed in domains ranging through medical sciences, biophysical sciences, precision agriculture, water management, smart manufacturing, smart transport, and environmental sciences. In such applications, sensor devices collect a vast quantity of application-specific measurement data such as patients’ vital signs, weather parameters, plant pathogens, vehicle movement and status, airborne pollutants, energy distribution, and water consumption and reserves. The number of such sensor devices are also increasing exponentially along with the adoption by different applications. In 2015, there are more than 4.9 billion connected IoT devices worldwide and the number is expected to reach more than 20.8 billion by 2020. However, ubiquitous deployment of IoT applications bring their own vulnerabilities. Unless security, privacy and trust features are built in during the design, deployment and operational phases, these systems can readily be compromised, making the IoT an easy target for attackers. There is a clear danger that the promising vision of IoT could instead become the chaos of an Internet of Vulnerable Things where critical decisions might be wrongly based on incorrect data acquired from poorly designed, faulty, or malicious devices. As more reliance is placed on large automated systems in future (for example, large-scale smart health care systems where life-critical decisions will demand high quality data), it is important to increase the confidence in IoT systems by addressing its security needs.
The IoT system must satisfy the following properties to meet its security needs. Confidentiality – the ability to locate the devices connected to the network and transmit the data from such devices without violating the privacy; Integrity – the ability to verify that the data is not modified without a proper authorization; and Authentication – the ability to verify the provenance of IoT devices without any attacks. The security properties should be met without compromising the performance. However, IoT system consists of lightweight devices, such as TI CC2538 modules, intermediate nodes and back-end servers. As stated above, lightweight sensor devices are used to collect and transmit data to intermediate nodes or to the server if a connection is available. Because lightweight devices are low-cost and resource constrained, traditional approaches are no longer applicable. In this project, we aim to address the authentication problem by devising a lightweight IoT device authentication solution: CSIRO Lightweight Authentication Protocol (CLAP). The CLAP also enables secure communication to lightweight devices through a public insecure network. The CLAP is being developed considering both security and performance concerns.
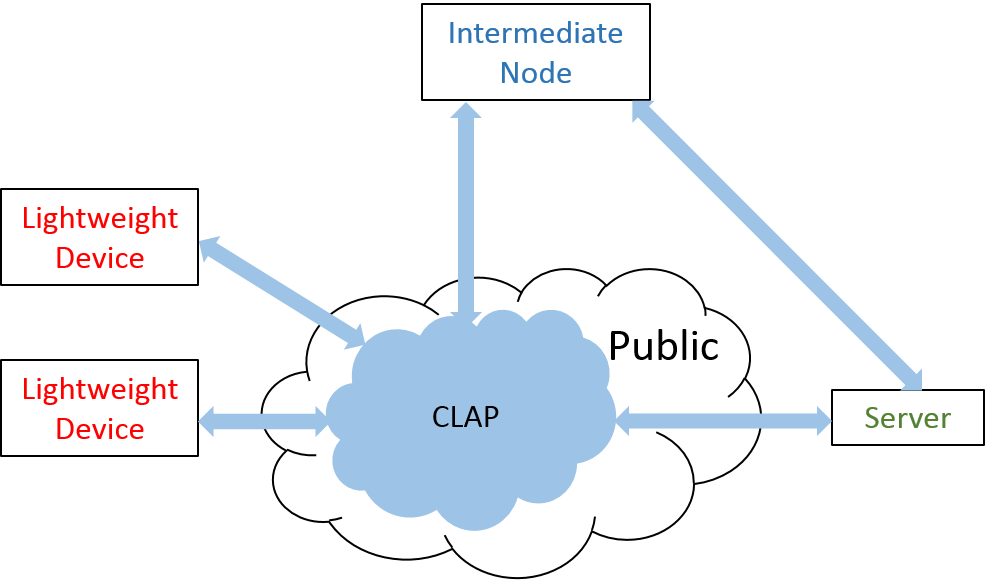
Fig 2: CLAP System Overview
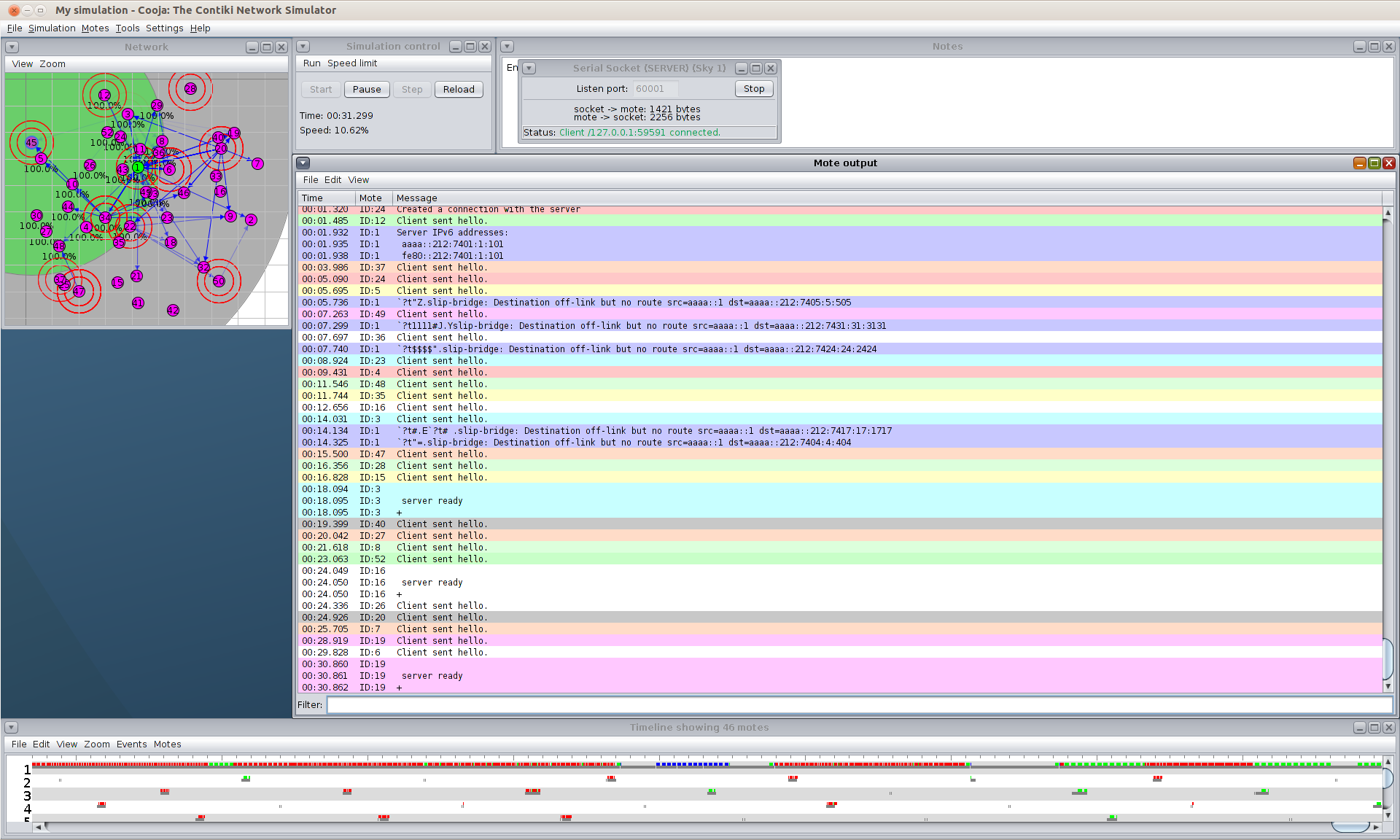
Fig 3: Emulation of CLAP
Features and Properties
Developing authentication protocols for lightweight devices is one of the most challenging tasks in IoT systems. CLAP provides the following security and performance features:
- Untraceability: A device is not traceable by unauthorised people.
- Anonymity: A device is fully anonymous against unauthorised people.
- Confidentiality: Transmitted data is protected by encryptions.
- Efficiency: The authentication is faster than existing solutions.
- Low-cost: Sensors can be lightweight passive device without battery.
- Scalability: CLAP supports large-scale applications.
- Compatibility: CLAP is compatible with existing security systems.
- Modular: CLAP can be easily installed and customised.
- The protocol is free from well-known attacks.
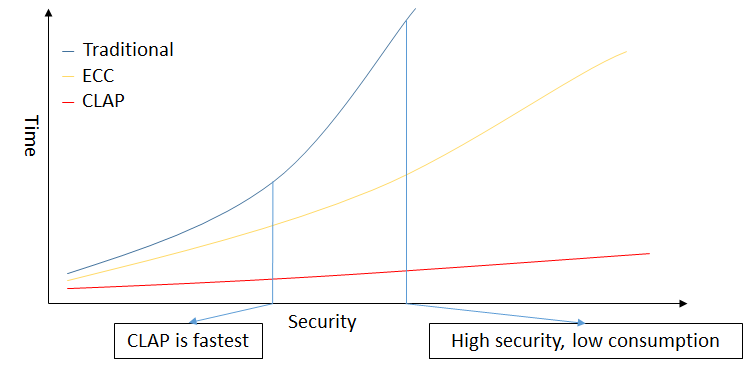
Fig 4: A Performance Comparison Sketch
Patent
- Dongxi Liu, Nan Li and Surya Nepal. “Asymmetric Cryptography and Authentication”, 2016901198.
Contact
Surya Nepal PhD
Principal Research Scientist | Distributed Systems Security
DATA61 | CSIRO
PO Box 76, Epping NSW 1710
T +61 2 9372 4256
