Encrypted Database Management
Database services in the cloud are attracting more companies to outsource their databases, since in this way the companies do not need to maintain their own database management systems. However, with such cloud services the companies lose the physical control to their databases and the privacy of outsourced data is always a concern. In this project, we have developed techniques that allow the companies to encrypt their databases before outsourcing, and moreover, the execution of standard SQL queries directly over encrypted databases.
Reasons to Encrypt Databases
- Databases are attractive attack targets, since a database usually collects a lot of information;
- Even if the database servers are compromised, databases are still under protection;
- Databases can be securely outsourced to clouds or other untrusted platforms.
Fig 1: Fragment of an Encrypted Database
Problems of Database Encryption
- Encrypted data is meaningless for DBMSs to query. A query usually needs to compare values for checking query conditions and aggregate numerical values to generate query results. The ciphertexts generated with the widely-sued encryption algorithm, such as AES, cannot be meaningfully compared and aggregated, hence hampering the existing DBMSs to execute query statements.
- It is not acceptable to decrypt a database before executing a query, since we do not want the untrusted cloud to own decryption keys. In addition, the data owners cannot decrypt a whole database by themselves, because it takes time to download a big database, and moreover data owners are not supposed to maintain the system to manage databases when the cloud database services are being used.
Our Techniques
Fig 2 shows the architecture of querying encrypted databases. Our techniques are implemented in the query proxy. An online demo is available at http://150.229.2.229/familySys/home.
- Homomorphic encryption is for aggregate queries (e.g., the total income of all families);
- Order-Preserving Indexing is for range queries (e.g., the families in a particular area);
- Query translation to make encrypted databases transparent to applications.
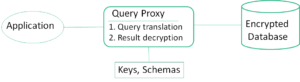
Fig 2: Architecture of Managing Encrypted Databases
Features of Our Solution
- The existing DBMSs, such as SQL Server and Oracle DB, can be used, without any extension and change;
- An expressive subset of SQL queries can be executed directly by DBMSs, such as complex aggregate queries and range queries;
- The result of aggregate queries is not bounded by our techniques, ensuring correctness of large query results for long-standing dynamic databases;
- Real numbers (not only positive integers) are directly encrypted for aggregation, convenient for application development.
Publications
- Dongxi Liu, Shenlu Wang. “Nonlinear order preserving index for encrypted database query in service cloud environments”, Concurrency and Computation: Practice and Experience 25(13): 1967-1984, 2013.
- Dongxi Liu, “Homomorphic Encryption for Database Querying”, International Patent Application No.: PCT/AU2013/000674, 2013.
- Dongxi Liu and Shenlu Wang. “DEMO: Query Encrypted Databases Practically”. Proc 19th ACM Conference on Computer and Communication Security (CCS 2012), Raleigh, NC, USA.
- Dongxi Liu, Shenlu Wang. “Programmable Order-Preserving Secure Index for Encrypted Database Query”, Proc. 5th IEEE International Conference on Cloud Computing (IEEE Cloud 2012), Honolulu, Hawaii, USA.
Conact:
Dongxi Liu
Distributed System Security
CSIRO Data61
Marsfield, NSW 2122
Phone: +61-2-9372-4152
Email: dongxi.liu@data61.csiro.au
