Behaviour Data Engineering and UEBA Cybersecurity
Behaviour Data Engineering and UEBA Cybersecurity
Overview
Behaviour Data Engineering plays an important role in intelligence creation under the fourth paradigm, the data-intensive scientific discovery. By collecting, aggregating, and analysing behaviour patterns of an entity (including human, things, events, …, etc.) together, deeper insights, from correlation to causations, can be possible through domain knowledge driven prescriptive analytics.
Different from traditional data mining, behaviour data engineering emphasizes on the followings:
- Behaviour Modeling and Profiling:
The behaviour operation model of an entity will first be defined using domain knowledge and ontological engineering techniques and then subsequently adapted through the discovery of new behaviour attributes using data mining techniques. The dynamic profile of the behaviour model of the entity will also be updated continuously using streaming data through monitoring.
- Behaviour Model Representation:
Behaviour model of an entity will be represented using some (hopefully standardized) structured information expression language. This is to facilitate the sharing of behaviour related information.
- Behaviour Coupling:
Using domain knowledge and advanced data mining techniques, inter-dependence relationship among behaviour data will be discovered/resolved and they will be used to update the behaviour model as well as to assist the subsequent behaviour analytics.
- Behaviour Analytics:
When performing analytics on the behaviour data sources, the emphasis of the analytics will be on both the co-relation patterns and the causations behind. This is to facilitate actionable decision for the prescriptive analytics.
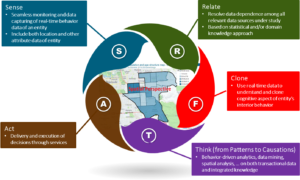
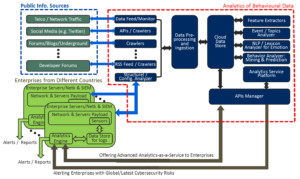
Applications
Currently, the two domains that we have been looking into are: (i) quality of life for ageing population, and (ii) user/event behaviour analytics for cybersecurity (shown in the figure below).
Contact: Chi-Hung Chi, chihung.chi<at>csiro.au
Selected Publications
- Chu,, Wong, R., Chi, C.H., Zhou, W., Ho, I., “The Design of a Cloud-based Tracker Platform Based on System-of-Systems Service Architecture,” Accepted in Information Systems Frontiers, 2016.
- Chu, V., Wong, R.K., Fong, S., Chi, C.H., “Emerging Service Orchestration Discovery and Monitoring,” accepted in the IEEE Transactions on Service Computing, September 2015. DOI:10.1109/TSC.2015.2511000
- Yu, Z., Wong, R.K., Chi, C.H., “Efficient Role Mining for Context-Aware Service Recommendation Using a High-Performance Cluster,” accepted in the IEEE Transactions on Service Computing, September 2015. DOI:10.1109/TSC.2015.2485988
- Wang, C., Chi, C.H., Zhou, W., Wong, R., “Coupled Interdependent Attribute Analysis on Mixed Data,” Proceedings of AAAI Conference on Artificial Intelligence, 2015.
- Wang, C., Dong, X.J., Zhou, F., Cao, L.B., Chi, C.H., “Coupled Attribute Similarity Learning on Categorical Data,” IEEE Transactions on Neural Networks and Learning Systems, Volume 26, Number 4, April, 2015.
- Wang, C., Cao, L.B., Chi, C.H., “Formalization and Verification of Group Behavior Interactions,” IEEE Transactions on Systems, Man and Cybernetics: Systems, 45, No. 8, August 2015.
- Zhao, Y.W., Chi, C.H., van den Heuvel, W.J., “Imperfect Referees: Reducing the Impact of Multiple Biases in Peer Review,” Journal of the American Society for Information Science and Technology, Volume 66, Number 11, 2015.
- Saleem, M.S., Ding, C., Liu, X., Chi, C.H., “Personalized Decision-Strategy based Web Service Selection using a Learning-to-Rank Algorithm,” IEEE Transactions on Services Computing, Volume 8, Number 5, Sept-Oct 2015.
- Chu, W., Wong, R., Chen, F., Chi, C.H., “Microblog Topic Contagiousness Measurement and Emerging Outbreak Monitoring,” Proceedings of the IEEE Conference on Information and Knowledge Management (CIKM), 2014.
- Zhou, W., Pierre, G., Chi, C.H., “CloudTPS: Scalable Transactions for Web Applications in the Cloud,” IEEE Transactions on Service Computing, Volume 5, Issue 4, November, 2012.
